Onwards to smooth VPN access
In early 2016 Santa Monica Networks made a decision to move away from sms authentication and Google authenticator to a more convenient yet secure solution for multi-factor VPN protection. The problem with the existing solution was that due to distraction from work and forgetting token at home, SMN lost up to 6000 EUR per employee per year in productivity:
- Manual code retyping distracted from the flow users and sometimes it took up to 20 minutes for the user to get back to the work he or she were doing;
- SMS is not secure enough when there is need for protecting sensitive data;
- Google Authenticator security depends on how securely is exchanged the initial code during onboarding – security is contradicting with convenience when user has to onboard himself remotely;
- The total security of the solution, when the key length is 6-8 symbols, is not adequate for accessing critical data.

“Just works”
Ugis Berzins, Chairman of the Board at Santa Monica Networks Latvia
From hardware tokens to mobile based solution
Santa Monica Networks have been working in the IT market since 1989. During all the years of its activity the company has accumulated great experience in the fields of data transmission networks, IT security and IP communications and recently started development of Data Center solutions business.
As SMN works with some of the most security aware companies such as governments and financial companies, we have always understood the importance of strong security. However, if the solution, which harms productivity, this might not only lead to inefficiencies but also to people looking for ways to bypass the security – leaving it vulnerable to data breaches. Choosing a solution for secure VPN access we SMN set these criteria:
- Meeting the Bring Your Own Device trend in the workplace – people want to use more and more their own mobile phones at work;
- Simple Integration with Active Directory;
- Adjustable security and onboarding policies – adding fingerprint, geolocation, additional PIN for authentication and choosing between manual and automatic user onboarding;
- On-premise installation.
Notakey does not make a compromise between strong security and user convenience. With the help of Notakey we could make multi-factor or multi-person authentication in one app.
- Ugis Berzins
Notakey is built in a way that it is easy to integrate and future-proof. It is built on PKI with a hardware level protection on the mobile phone. This means that is interoperable with all the existing systems used by governments and large organisations. As we use electronic signatures for authentication, new features such as document signature can be easily added to the already existing solution. With Notakey SMN can focus on what they do the best, while being sure that Notakey team takes care of ever evolving security needs.
What exactly was implemented at SMN
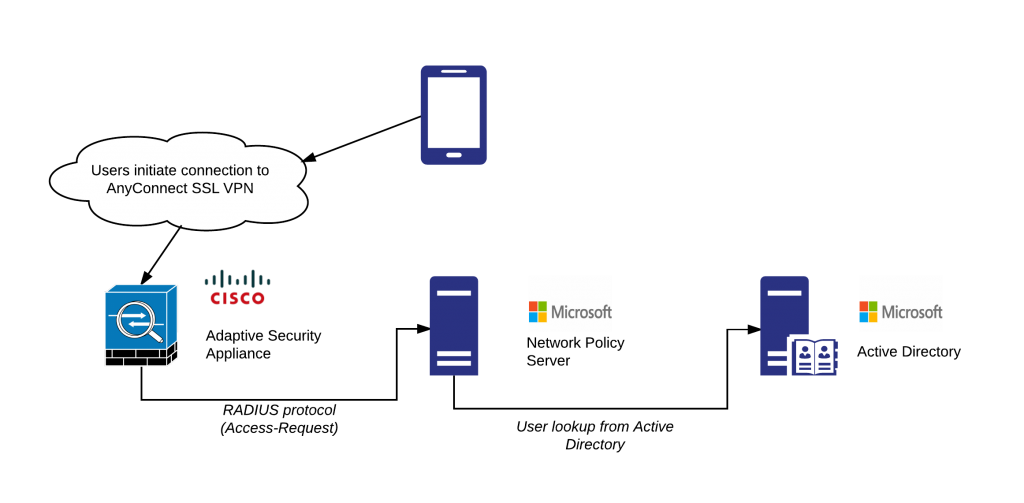
Before
-Santa Monica Networks uses Cisco ASA. Employees access the internal network via Cisco AnyConnect SSL VPN, which verifies users against Microsoft Network Policy Server (NPS) via the RADIUS protocol. NPS verifies users against the corporate Active Directory.
–Problem: this way the user only is verified with a single factor. Santa Monica Networks experimented with SMS-based solutions, as well as Google Authenticator, but encountered resistance from users. These solutions would not support easy enrollment, were not flexible enough and could not be centrally managed with advanced security policies.
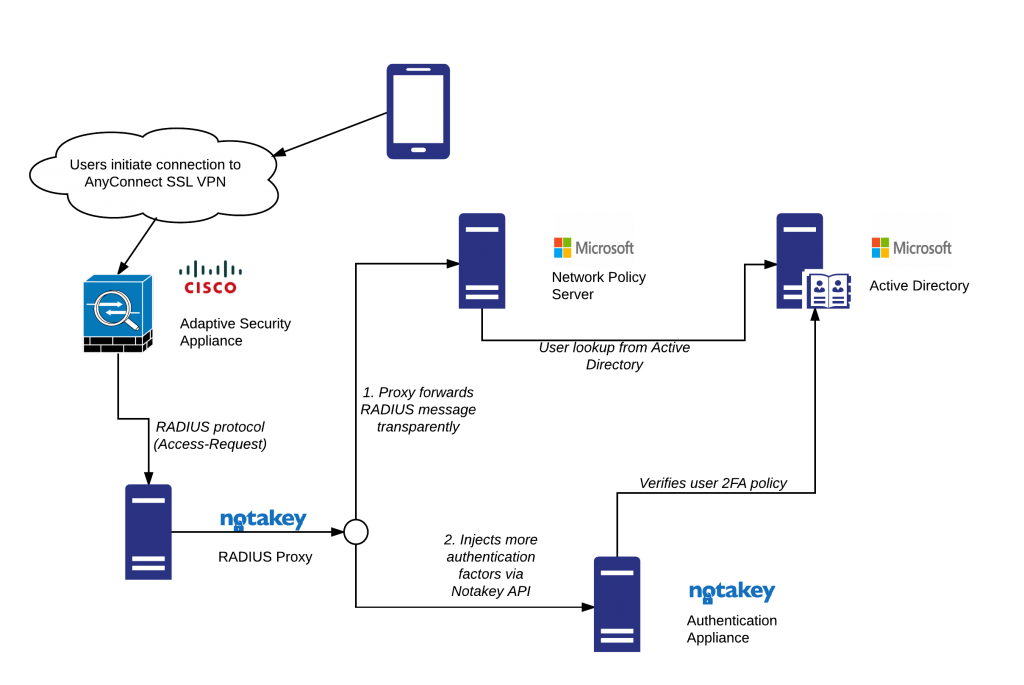
After
–Solution: to implement Notakey, Santa Monica Networks deployed the Notakey on-premise authentication appliance. This appliance allows sourcing users from various sources (such as Active Directory), and specifying security policies – such as allowed user groups, and onboarding requirements for employee self-enrollment.
-To transparently upgrade their existing setup, Santa Monica Networks additionally deployed a RADIUS proxy on their Microsoft Network Policy Server servers. This piece of software accepts RADIUS packets, forwards them to the existing RADIUS server, and if they are approved – adds Notakey-based verification on top.
–All without any changes to the existing setup!
*Thanks to Rietumu Bank for the photo.

